Home /
Expert Answers /
Computer Science /
build-the-attack-tree-for-the-attack-described-in-this-exercise-the-attack-targets-the-destruction-pa898
(Solved): Build the attack tree for the attack described in this exercise. The attack targets the destruction ...
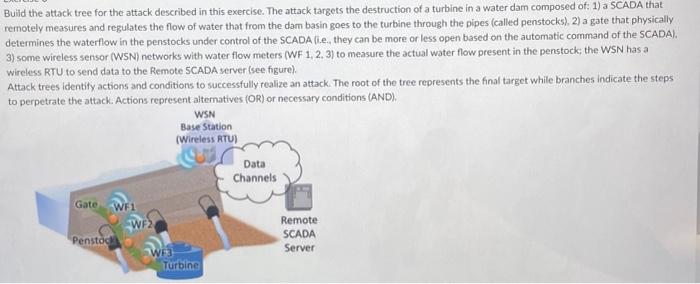

Build the attack tree for the attack described in this exercise. The attack targets the destruction of a turbine in a water dam composed of: 1) a SCADA that remotely measures and regulates the flow of water that from the dam basin goes to the turbine through the pipes (called penstocks), 2) a gate that physically determines the waterflow in the penstocks under control of the SCADA (i.e., they can be more or less open based on the automatic command of the SCADA). 3) some wireless sensor (WSN) networks with water flow meters (WF 1, 2, 3) to measure the actual water flow present in the penstock; the WSN has a wireless RTU to send data to the Remote SCADA server (see figure). Attack trees identify actions and conditions to successfully realize an attack. The root of the tree represents the final target while branches indicate the steps to perpetrate the attack. Actions represent altematives (OR) or necessary conditions (AND).
Assumption for the attack (precondition) is that the attacker has access to some hosts in the remote station and can plug a USB device in (e.g. he/she is an employee at the remote control facility) and has tools to exploit SCADA soltware and server host vulnerabilities. Final Goal (Goal 0 ) of Attack Tree indicates that the attack target is the turbine destruction. Goal 1 accomplishes Goal 0 by overloading the Penstock (the water pipe from the dam basin to the turbine) with excess water. Goal 2 indicates three altematives to realize this: 1) physically breaking the dam gate controlling the water sent to the penstock; 2) excessively opening the gate by sending an explicit command to the gate actuator (i.e. a motor that opens the gate from remote with a signal); 3) altering the data messages from water flow sensors to the SCADA for example reporting low measurement levels of water flows while they are actually high: this indeed will solicit additional gate opening to feed the turbine. Goal 3 indicates necessary action to alter water flow measurements, particularly when they are collected from nodes of a Wireless: Sensor Network: 1) usage of malicious software from a pen drive on some host in the remote facility to locate and exploit SCADA server vulnerabilities; 2) creation of a backdoor on the SCADA server; 3 ) gathering of information related to the RTU device and network infrastructure (6.e, IP addres; of 85 hosts): 4) scanning and violation of the BS host: 5) access to the BS host and installation of a malicious Over-The-Air (OTA) program which reprograms sensors with a rogue (li.e., malicious) code.